This requires Entra ID P1 licensing to work. The first method is manual and requires you to authenticate each time you want to download the logs. You can tweak the output as needed.
2
3
4
5
$logs = Get-MgAuditLogSignIn -All | Select-Object CreatedDateTime, AppDisplayName, ClientAppUsed, ConditionalAccessStatus, @{Name="DeviceName";Expression={$_.DeviceDetail.DisplayName}}, UserDisplayName, UserPrincipalName, @{Name="City";Expression={$_.Location.City}}, @{Name="Country";Expression={$_.Location.CountryOrRegion}}, IPAddress, @{Name="ErrorCode";Expression={$_.Status.ErrorCode}}, @{Name="ErrorInfo";Expression={$_.Status.AdditionalDetails}}
$logs | Export-Csv -Path "C:\Export\SignInLogs.csv" -NoTypeInformation
If you want to run this as a scheduled task and therefore won’t be able to manually authenticate each time, then you can create a self-signed certificate and an app registration in Microsoft Entra and use that instead. The following steps create a 2 year self-signed certificate that you’ll be able to use for this purpose.
You’ll then need to export the certificate somewhere:
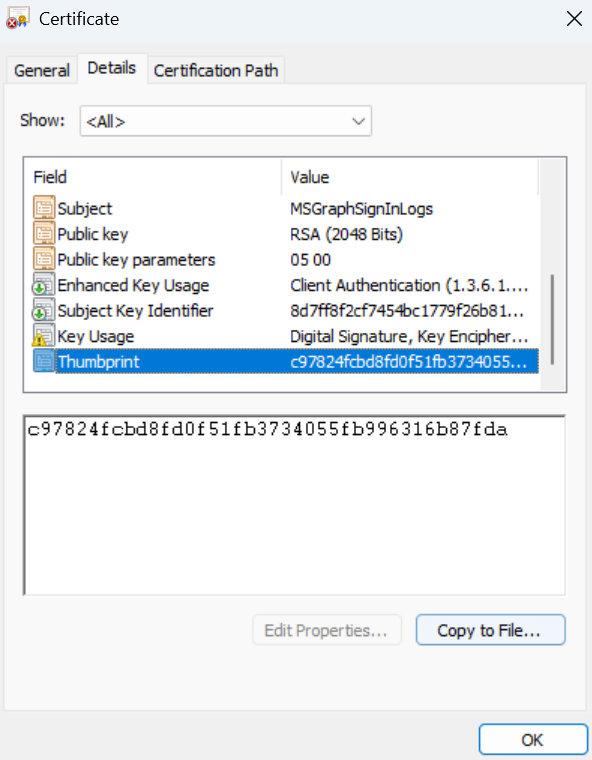
Open the certificate and copy the Certificate Thumbprint:
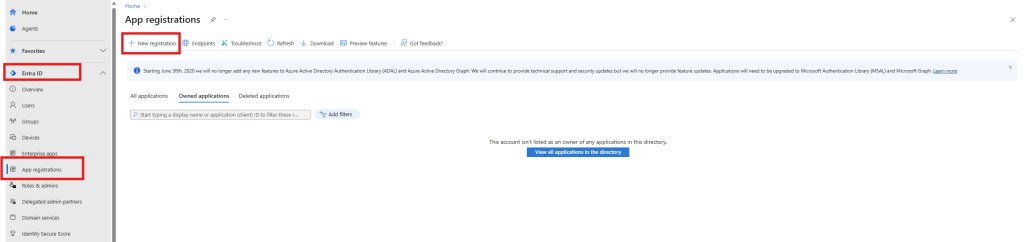
Now create an App Registration in Entra ID
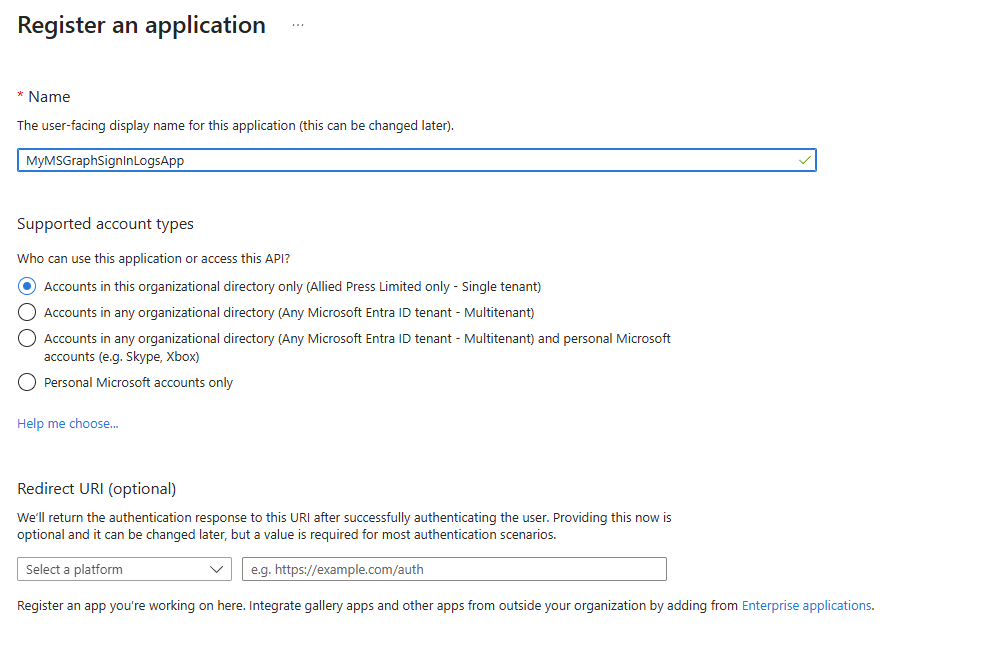
Give the app an appropriate name and click “Register”, leave the other settings as default.
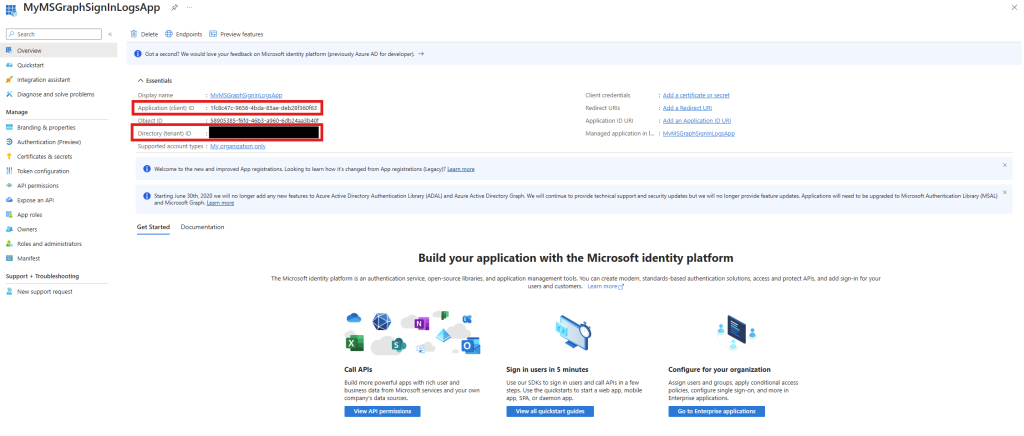
Once the app is created, save the generated Application (client) ID and the Directory (tenant) ID somewhere:
In the left menu pane, click in API Permissions, then click on Microsoft Graph (1) and then Application permissions:
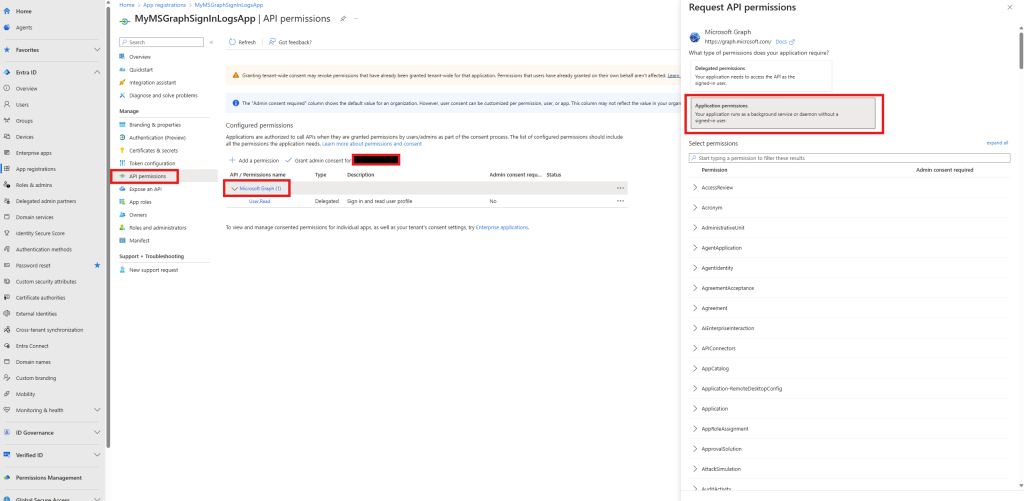
Add the following permission “AuditLog.Read.All” and then click Update permissions

Once you have added in the permissions, click “Grant admin consent for…” to provide the necessary access.

Now move to the Certificates and secrets section in the menu pane and then select Certificates and Upload certificate:
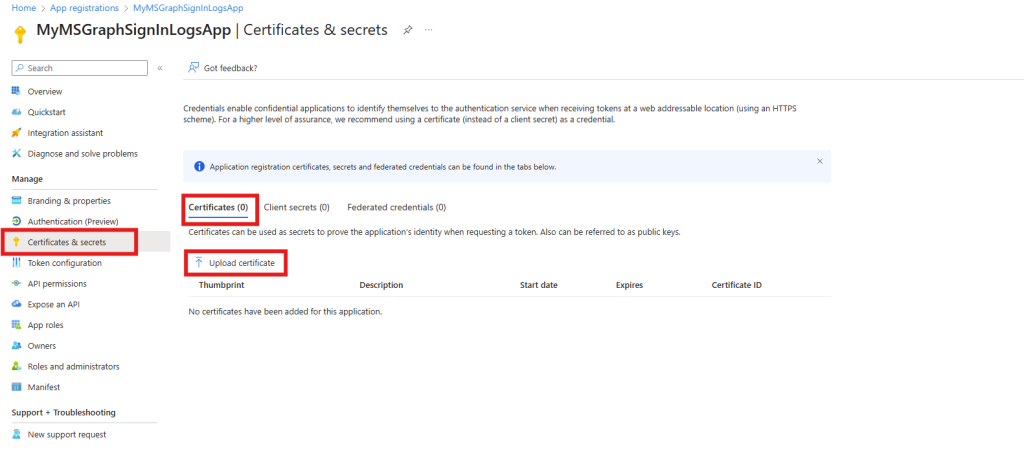
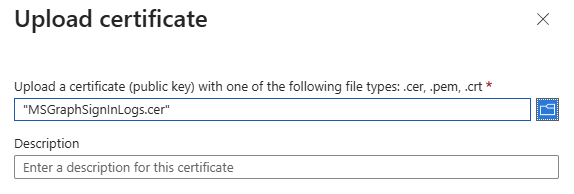
Locate the certificate file you exported earlier and then click Add
This completes the steps in Microsoft Entra ID – now we can write the following PowerShell to complete the authentication using the certificate and app registration using the information you saved earlier and the rest of the script from above remains the same:
2
3
4
5
$logs = Get-MgAuditLogSignIn -All | Select-Object CreatedDateTime, AppDisplayName, ClientAppUsed, ConditionalAccessStatus, @{Name="DeviceName";Expression={$_.DeviceDetail.DisplayName}}, UserDisplayName, UserPrincipalName, @{Name="City";Expression={$_.Location.City}}, @{Name="Country";Expression={$_.Location.CountryOrRegion}}, IPAddress, @{Name="ErrorCode";Expression={$_.Status.ErrorCode}}, @{Name="ErrorInfo";Expression={$_.Status.AdditionalDetails}}
$logs | Export-Csv -Path "C:\Export\SignInLogs.csv" -NoTypeInformation